Bluetooth security at risk with new brute-force attack method
Robert Triggs / Android Authority
TL;DR
- A French research team with EURECOM has discovered a scary Bluetooth security flaw.
- Using a brute-force attack, a man-in-the-middle (MitM) operator could spoof two connected devices using Bluetooth 4.2 or newer.
- The Bluetooth SIG has acknowledged the flaw and made suggestions for OEMs to keep consumers safe.
With smartphones rarely incorporating headphone jacks anymore, billions of users have had to rely on Bluetooth headsets for their audio needs. Historically, this has been secure. There’s an encrypted connection between your phone and your headset, for example.
However, a French team at EURECOM has found a significant flaw in the security between two devices connected via Bluetooth. As first spotted by Bleeping Computer, the published paper on this exploit shows a relatively simple method for brute-force attacking the BT encryption keys between two devices. If successful, the attacker could spoof the devices and access potentially sensitive data.
This exploit appears to work at least partially on any device using Bluetooth 4.2 or newer. For the record, Bluetooth 4.2 support rolled out in late 2014, so most aspects of this attack would theoretically work on pretty much every modern Bluetooth device.
The team divided the attacks into six different styles, with the acronym BLUFFS used to summarize all of them. As part of the published paper, the EURECOM team — led by Daniele Antonioli — showed a table of the devices they were able to spoof using these attacks and how successful each of the six types was. The table is…sobering, to say the least:
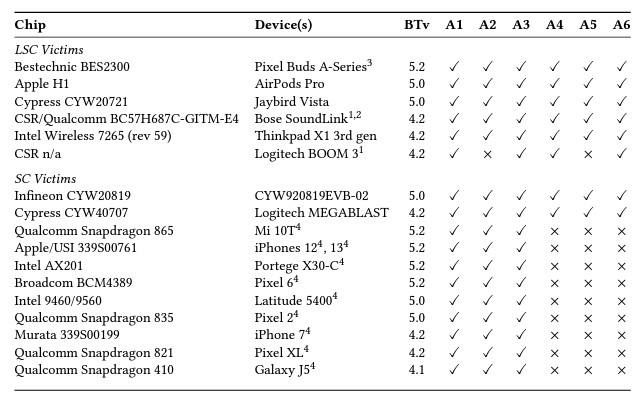
Thankfully, Antonioli and co. are being very open about their discoveries. The team has a GitHub page with plenty of information for anyone who is interested.
Meanwhile, the Bluetooth Special Interest Group (SIG), the non-profit agency overseeing the standard’s development, has acknowledged EURECOM’s findings. In a security bulletin, the Bluetooth SIG suggests OEMs instituting Bluetooth technology in products follow strict security protocols to prevent this attack from working. However, it does not mention if upcoming versions of Bluetooth will patch this exploit. The most recent BT standard is v5.4, which was launched in February.
Source link
